Block chain Technology
What is Blockchain?
A Blockchain is a digital ledger of transactions that is secure, immutable, and decentralized. It consists of a chain of blocks and each block contains a secure group of transactions of money, bitcoins, contracts, property, etc. without any need for third-party middle-man such as central authorities, banks, government, etc. Transactions are verified by a network of computers. Once a block of information is created in the chain, it can’t be changed or deleted. This makes the blockchain very secure and trustworthy. It is a software protocol, it never runs without the internet.
Why Do We Use Blockchain?
There is no need for centralized authorities to verify our transactions. Blockchain makes it decentralized and secure. The security is maintained by cryptographic processes performed by p2p users, through the process called Data mining. Some of its important features are:
- Secure
- Transparent
- Tamper-proof
- Peer-to-peer transaction
How does Blockchain Technology Work?
One of the famous use of Blockchain is Bitcoin. Bitcoin is a cryptocurrency and is used to exchange digital assets online. Bitcoin uses cryptographic proof instead of third-party trust for two parties to execute transactions over the Internet. Each transaction protects through a digital signature.
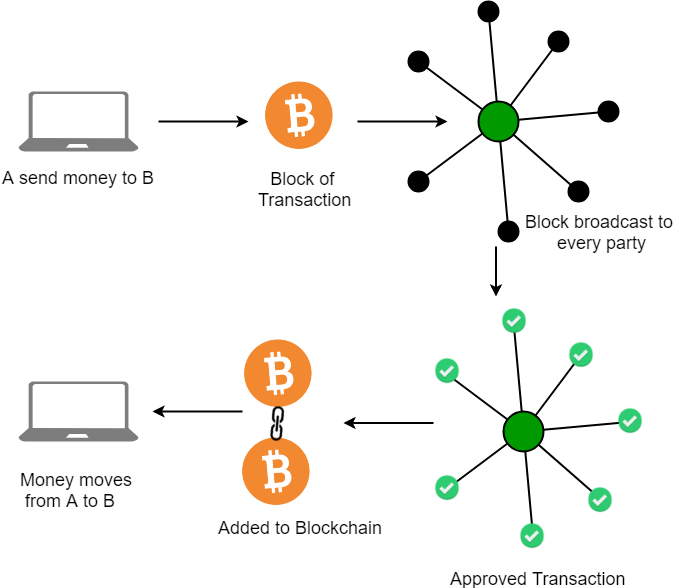
Blockchain nodes
A node is a computer connected to the Blockchain Network. Node gets connected with Blockchain using the client. The client helps in validating and propagating transactions onto the Blockchain. When a computer connects to the Blockchain, a copy of the Blockchain data gets downloaded into the system and the node comes in sync with the latest block of data on Blockchain. The Node connected to the Blockchain which helps in the execution of a Transaction in return for an incentive is called Miners.
Disadvantages of the current transaction system:
- Cash can only be used in low-amount transactions locally.
- The huge waiting time in the processing of transactions.
- The need for a third party for verification and execution of Transactions makes the process complex.
- If the Central Server like Banks is compromised, the whole system is affected including the participants.
- Organizations doing validation charge high process thus making the process expensive.
Building trust with Blockchain: Blockchain enhances trust across a business network. Blockchain builds trust through the following five attributes:
- Distributed: The distributed ledger is shared and updated with every incoming transaction among the nodes connected to the Blockchain. All this is done in real time as there is no central server controlling the data.
- Secure: There is no unauthorized access to Blockchain made possible through Permissions and Cryptography.
- Transparent: Because every node or participant in Blockchain has a copy of the Blockchain data, they have access to all transaction data. They themselves can verify the identities without the need for mediators.
- Consensus-based: All relevant network participants must agree that a transaction is valid. This is achieved through the use of consensus algorithms.
- Flexible: Smart Contracts which are executed based on certain conditions can be written into the platform. Blockchain Networks can evolve in pace with business processes.
Benefits of Blockchain
- Time-saving: No central Authority verification is needed for settlements making the process faster and cheaper.
- Cost-saving: A Blockchain network reduces expenses in several ways. No need for third-party verification. Participants can share assets directly. Intermediaries are reduced. Transaction efforts are minimized as every participant has a copy of the shared ledger.
- Tighter security: No one can tamper with Blockchain Data as it is shared among millions of Participants. The system is safe against cybercrimes and Fraud.
- Collaboration: It permits every party to interact directly with one another while not requiring third-party negotiation.
- Reliability: Blockchain certifies and verifies the identities of every interested party. This removes double records, reducing rates and accelerating transactions.
Application of Blockchain
- Leading Investment Banking Companies like Credit Suisse, JP Morgan Chase, Goldman Sachs, and Citigroup have invested in Blockchain and are experimenting to improve the banking experience and secure it.
- Following the Banking Sector, the Accountants are following the same path. Accountancy involves extensive data, including financial statements spreadsheets containing lots of personal and institutional data. Therefore, accounting can be layered with blockchain to easily track confidential and sensitive data and reduce human error and fraud. Industry Experts from Deloitte, PwC, KPMG, and EY are proficiently working and using blockchain-based software.
- Booking a Flight requires sensitive data ranging from the passenger’s name, credit card numbers, immigration details, identification, destinations, and sometimes even accommodation and travel information. So sensitive data can be secured using blockchain technology. Russian Airlines are working towards the same.
- Various industries, including hotel services, pay a significant amount ranging from 18-22% of their revenue to third-party agencies. Using blockchain, the involvement of the middleman is cut short and allows interaction directly with the consumer ensuring benefits to both parties. Winding Tree works extensively with Lufthansa, AirFrance, AirCanada, and Etihad Airways to cut short third-party operators charging high fees.
- Barclays uses Blockchain to streamline the Know Your Customer (KYC) and Fund Transfer processes while filling patents against these features.
- Visa uses Blockchain to deal with business-to-business payment services.
- Unilever uses Blockchain to track all their transactions in the supply chain and maintain the product’s quality at every stage of the process.
- Walmart has been using Blockchain Technology for quite some time to keep track of their food items coming right from farmers to the customer. They let the customer check the product’s history right from its origin.
- DHL and Accenture work together to track the origin of medicine until it reaches the consumer.
- Pfizer, an industry leader, has developed a blockchain system to keep track of and manage the inventory of medicines.
- The government of Dubai looking forward to making Dubai the first-ever city to rely on entirely and work using blockchain, even in their government office.
- Along with the above organizations, leading tech companies like Google, Microsoft, Amazon, IBM, Facebook, TCS, Oracle, Samsung, NVIDIA, Accenture, and PayPal, are working on Blockchain extensively.
Blockchain project ideas
Here are a few project ideas for beginners looking to learn more about blockchain technology:
- Cryptocurrency Wallet: Create a simple cryptocurrency wallet application that allows users to send and receive digital assets.
- Blockchain Explorer: Develop a web-based application that allows users to view and search the transactions on a specific blockchain.
- Smart Contract: Implement a simple smart contract on the Ethereum blockchain that can be used to manage a digital token or asset.
- Voting System: Create a blockchain-based voting system that allows for secure and transparent voting while maintaining voter anonymity.
- Supply Chain Management: Develop a blockchain-based system for tracking the movement of goods and services through a supply chain, providing greater transparency and traceability.
- Decentralized marketplace: Create a decentralized marketplace using blockchain technology where the goods and services can be directly bought by the customers without any intermediary.
- Identity Management: Create a decentralized digital identity management system that allows users to control their personal information and share it securely with others.
Future Scope of Blockchain Technology
The following are some potential uses for blockchain in the future:
- Digital Identity: Blockchain-based digital IDs might be used to store personal data safely and securely as well as offer a means of establishing identity without the need for a central authority.
- Smart Contracts: A variety of legal and financial transactions could be automated using smart contracts, self-executing contracts with the terms of the agreement put straight into lines of code.
- Decentralized Finance (DeFi): Using blockchain technology, decentralized financial systems might be built that support peer-to-peer transactions and do away with conventional intermediaries like banks.
- Supply Chain Management: Blockchain technology can be applied to a permanent record of how goods and services have been moved, enabling improved openness and traceability across the whole supply chain.
- Internet of Things (IoT): Blockchain technology may be used to build decentralized, secure networks for IoT devices, enabling them to exchange data and communicate with one another in an anonymous, safe manner.
In general, blockchain technology is still in its early stages and has a wide range of potential applications.
Advantages of Blockchain Technology:
- Decentralization: The decentralized nature of blockchain technology eliminates the need for intermediaries, reducing costs and increasing transparency.
- Security: Transactions on a blockchain are secured through cryptography, making them virtually immune to hacking and fraud.
- Transparency: Blockchain technology allows all parties in a transaction to have access to the same information, increasing transparency and reducing the potential for disputes.
- Efficiency: Transactions on a blockchain can be processed quickly and efficiently, reducing the time and cost associated with traditional transactions.
- Trust: The transparent and secure nature of blockchain technology can help to build trust between parties in a transaction.
Disadvantages of Blockchain Technology:
- Scalability: The decentralized nature of blockchain technology can make it difficult to scale for large-scale applications.
- Energy Consumption: The process of mining blockchain transactions requires significant amounts of computing power, which can lead to high energy consumption and environmental concerns.
- Adoption: While the potential applications of blockchain technology are vast, adoption has been slow due to the technical complexity and lack of understanding of the technology.
- Regulation: The regulatory framework around blockchain technology is still in its early stages, which can create uncertainty for businesses and investors.
- Lack of Standards: The lack of standardized protocols and technologies can make it difficult for businesses to integrate blockchain technology into their existing systems.
1. Immutable
Immutability means that the blockchain is a permanent and unalterable network. Blockchain technology functions through a collection of nodes. Once a transaction is recorded on the blockchain, it cannot be modified or deleted. This makes the blockchain an immutable and tamper-proof ledger that provides a high degree of security and trust.
- Every node in the network has a copy of the digital ledger. To add a transaction every node checks the validity of the transaction and if the majority of the nodes think that it is a valid transaction then it is added to the network. This means that without the approval of a majority of nodes no one can add any transaction blocks to the ledger.
- Any validated records are irreversible and cannot be changed. This means that any user on the network won’t be able to edit, change or delete it.
2. Distributed
All network participants have a copy of the ledger for complete transparency. A public ledger will provide complete information about all the participants on the network and transactions. The distributed computational power across the computers ensures a better outcome.
Distributed ledger is one of the important features of blockchains due to many reasons like:
- In distributed ledger tracking what’s happening in the ledger is easy as changes propagate really fast in a distributed ledger.
- Every node on the blockchain network must maintain the ledger and participate in the validation.
- Any change in the ledger will be updated in seconds or minutes and due to no involvement of intermediaries in the blockchain, the validation for the change will be done quickly.
- If a user wants to add a new block then other participating nodes have to verify the transaction. For a new block to be added to the blockchain network it must be approved by a majority of the nodes on the network.
- In a blockchain network, no node will get any sort of special treatment or favors from the network. Everyone will have to follow the standard procedure to add a new block to the network.
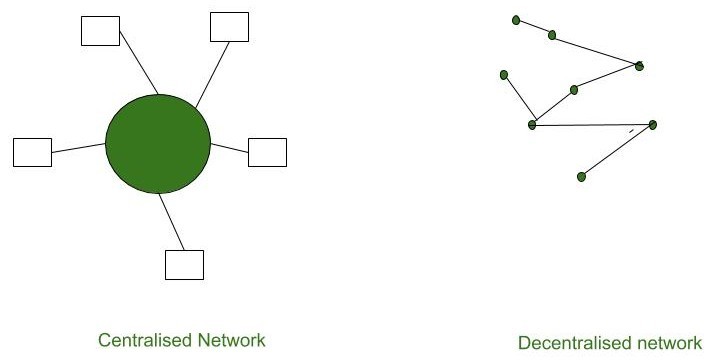
3. Decentralized
Blockchain technology is a decentralized system, which means that there is no central authority controlling the network. Instead, the network is made up of a large number of nodes that work together to verify and validate transactions. Each and every node in the blockchain network will have the same copy of the ledger.
Decentralization property offers many advantages in the blockchain network:
- As a blockchain network does not depend on human calculations it is fully organized and fault-tolerant.
- The blockchain network is less prone to failure due to the decentralized nature of the network. Attacking the system is more expensive for the hackers hence it is less likely to fail.
- There is no third-party involved hence no added risk in the system.
- The decentralized nature of blockchain facilitates creating a transparent profile for every participant on the network. Thus, every change is traceable, and more concreate.
- Users now have control over their properties and they don’t have to rely on third-party to maintain and manage their assets.
4. Secure
All the records in the blockchain are individually encrypted. Using encryption adds another layer of security to the entire process on the blockchain network. Since there is no central authority, it does not mean that one can simply add, update or delete data on the network.
Every information on the blockchain is hashed cryptographically which means that every piece of data has a unique identity on the network. All the blocks contain a unique hash of their own and the hash of the previous block. Due to this property, the blocks are cryptographically linked with each other. Any attempt to modify the data means to change all the hash IDs which is quite impossible.
5. Consensus
Every blockchain has a consensus to help the network to make quick and unbiased decisions. Consensus is a decision-making algorithm for the group of nodes active on the network to reach an agreement quickly and faster and for the smooth functioning of the system. Nodes might not trust each other but they can trust the algorithm that runs at the core of the network to make decisions. There are many consensus algorithms available each with its pros and cons. Every blockchain must have a consensus algorithm otherwise it will lose its value.
6. Unanimous
All the network participants agree to the validity of the records before they can be added to the network. When a node wants to add a block to the network then it must get majority voting otherwise the block cannot be added to the network. A node cannot simply add, update, or delete information from the network. Every record is updated simultaneously and the updations propagate quickly in the network. So it is not possible to make any change without consent from the majority of nodes in the network.
7. Faster Settlement
Traditional banking systems are prone to many reasons for fallout like taking days to process a transaction after finalizing all settlements, which can be corrupted easily. On the other hand, blockchain offers a faster settlement compared to traditional banking systems. This blockchain feature helps make life easier.
Blockchain technology is increasing and improving day by day and has a really bright future in the upcoming years. The transparency, trust, and temper proof characteristics have led to many applications of it like bitcoin, Ethereum, etc. It is a pillar in making the business and governmental procedures more secure, efficient, and effective.
Important Blockchain terminologies
- Node –A member of the Blockchain network.
- Address –An address is a string of alphanumeric characters which identify an entity in the blockchain network. Used to send and receive cryptocurrency transactions.
- A ledger which is maintained on many nodes in a decentralized network. The records are stored in a chronological order. This ledger can be of two types : Permissioned and Unpermissioned based on who has the access to view the ledger.
- Also short termed as P2P. As the name suggests, interactions that happen between two peers(parties/entities) in a highly interconnected network.
- Block –A block is a data structure that contains all the necessary metadata about the block(Block Header) itself and contains transactions. The first block in a blockchain is called the genesis block.
- block height –Block height is the number of blocks connected in the blockchain. Block height is a usually measure of the amount of data in the blockchain.
- A chain of blocks which contain some metadata about the block, some transactions and joined to the previous block by the previous block’s hash value.
- Block explorer –A tool to see statistics of a block in a blockchain. You can visit this link for the block explorer of Bitcoin and Ethereum.
- Hash –Performing a hash function on the output data in a blockchain is termed as hash. Commonly used in sentences like “the hash of “geeksforgeeks file is 142c53v2v31vc1526v35v63v5v4”. Used in verifying cryptocurrency transactions.
- Hash rate –Performance of a computer mining is measured in hashes per second or hash rate.
- A function that takes a variable-size input and output is a fixed-size unique value. SHA-256 algorithm is a cryptographic hash function example.
- Mining –Process of solving a complex mathematical problem in order to attach the new block of transactions to the blockchain. This term is used in reference to blockchains that use Proof-of-Work as consensus mechanism. But general use of this term is prevalent too.
- Difficulty –Hardness with which a new block of transactions can be connected to the blockchain. In Bitcoin, the difficulty is adjusted every 2016 blocks to keep the time of mining a new block at about 10 minutes.
- Block reward –Reward that is given to the entity which connects the new block to the blockchain. In the case of Bitcoin, miners get a reward of 12.5 Bitcoins for attaching new block to the blockchain. In the case of Peercoin, miners get a reward of 42.64 (at the time of writing this article) Peercoins for attaching a new block of transactions to the blockchain.
- A formal of digital asset which is regulated and transacted on the blockchain network. Encryption techniques are used to regulate the cryptocurrency, hence the name.
- Satoshi –The smallest recordable unit of currency in the Bitcoin. Currently, a satoshi is numerically equal to 0.00000001 BTC.
- Altcoin –An alternative to Bitcoin (ALTernative COIN). A famous altcoin is Litecoin.
- Wallet –A wallet is a file that contains the private keys of an entity. A wallet provides an interface to view and do transactions on the blockchain. Different wallets for different type of blockchains.
- Consensus is a way for all the nodes in a network to agree on the shared state of the ledger (list of transactions). Some common consensus mechanisms are Raft, Paxos, Byzantine Fault Tolerance algorithm, Proof-of-Work(PoW), Proof-of-Stake (PoS), etc.
- A smart contract has details and permissions written in code that require an exact sequence of events to take place to trigger the agreement of the terms mentioned in the smart contract. It can also include the time constraints that can introduce deadlines in the contract. Also known as cryptocontract and digital contract. It was first put forward by Nick Szabo in 1994.
- Transaction –An exchange of assets between two parties/entities.
- Transaction Fee –A part of the digital asset (cryptocurrency) that is charged from the parties who perform that transaction as a way to pay the networks who invest their resources in order to sustain the blockchain. In a proof of stake based blockchain (like Peercoin). the transaction fee is transferred to the minter/forger once he validates the new block of transactions successfully.
- An act of blockchain software update which leads to splitting of a blockchain into two or more valid blockchains. There are three common types of forks in blockchain, namely, hard fork, soft fork, temporary/accidental fork.
- 51% attack –An attack in which a single organization (of entities) performs invalid activities on the blockchain network because they control 51% of the network’s resources. In the Bitcoin network, it refers to owning 51% of miners. In Peercoin, it refers to owning 51% of peercoins.
- Double Spend –An act of using the same digital asset (cryptocurrency) twice. Its a common type of attack in blockchains. This type of attack becomes more difficult with increasing members that add the new block to the chain.
- Confirmation –The confirmation is the act of successfully adding a transaction to the blockchain after verification. As a rule of thumb, more confirmations means more security against a double spend attack (permanency).
- Testnet –As the name suggests, a Bitcoin test blockchain which is used by the network developers to carry out tests so that the main blockchain network is not affected. Assets in a testnet do not have any value. There have been three generations of testnet at the time of writing this article i.e., Testnet1, Testnet2, Testnet3 (currently).
- dApp –Full form : decentralized Application. An application that is open sourced which is operated anonymously and has its data stored on a blockchain. It must have some kind of incentive for the members who help to construct the blockchain.
- ASIC –Full form : Application Specific Integrated Circuit. These are a type of computers which are designed for performing a special task. In the case of Bitcoin, ASIC computers are used to solve SHA-256 hashing problem which help to connect the new blocks to the blockchain.
Permissionless Blockchain
It is also known as trustless or public blockchains, are available to everyone to participate in the blockchains process that use to validate transactions and data. These are used in the network where high transparency is required.
Characteristics:
- Permissionless blockchain has no central authority.
- The platform is completely open-source.
- Full transparency of the transaction.
- Heavy use of tokens.
Advantages:
- Everyone can participate only requirement is good hardware and internet.
- Bring trust among users or entities.
- It has a high level of transparency as it’s a larger network.
- Broader decentralization of access to more participants.
Disadvantages:
- Poor energy efficiency due to large network.
- Lower performance scalability.
- Less privacy as many of the things is visible.
Permissioned Blockchain
These are the closed network only a set of groups are allowed to validate transactions or data in a given blockchain network. These are used in the network where high privacy and security are required.
Characteristics:
- A major feature is a transparency based on the objective of the organization.
- Another feature is the lack of anatomy as only a limited number of users are allowed.
- It does not have a central authority.
- Developed by private authority.
Advantages:
- This blockchain tends to be faster as it has some nodes for validations.
- They can offer customizability.
- Strong Privacy as permission is needed for accessing transaction information.
- As few nodes are involved performance and scalability are increased.
Disadvantages:
- Not truly decentralized as it requires permission
- Risk of corruption as only a few participants are involved.
- Anytime owner and operator can change the rules as per their need.
Types of Blockchain
There are 4 types of blockchain:
- Public Blockchain.
- Private Blockchain.
- Hybrid Blockchain.
- Consortium Blockchain.
1. Public Blockchain
These blockchains are completely open to following the idea of decentralization. They don’t have any restrictions, anyone having a computer and internet can participate in the network.
- As the name is public this blockchain is open to the public, which means it is not owned by anyone.
- Anyone having internet and a computer with good hardware can participate in this public blockchain.
- All the computer in the network hold the copy of other nodes or block present in the network
- In this public blockchain, we can also perform verification of transactions or records
Advantages:
- Trustable: There are algorithms to detect no fraud. Participants need not worry about the other nodes in the network
- Secure: This blockchain is large in size as it is open to the public. In a large size, there is greater distribution of records
- Anonymous Nature: It is a secure platform to make your transaction properly at the same time, you are not required to reveal your name and identity in order to participate.
- Decentralized: There is no single platform that maintains the network, instead every user has a copy of the ledger.
Disadvantages:
- Processing: The rate of the transaction process is very slow, due to its large size. Verification of each node is a very time-consuming process.
- Energy Consumption: Proof of work is high energy-consuming. It requires good computer hardware to participate in the network
- Acceptance: No central authority is there so governments are facing the issue to implement the technology faster.
Use Cases: Public Blockchain is secured with proof of work or proof of stake they can be used to displace traditional financial systems. The more advanced side of this blockchain is the smart contract that enabled this blockchain to support decentralization. Examples of public blockchain are Bitcoin, Ethereum.
2. Private Blockchain
These blockchains are not as decentralized as the public blockchain only selected nodes can participate in the process, making it more secure than the others.
- These are not as open as a public blockchain.
- They are open to some authorized users only.
- These blockchains are operated in a closed network.
- In this few people are allowed to participate in a network within a company/organization.
Advantages:
- Speed: The rate of the transaction is high, due to its small size. Verification of each node is less time-consuming.
- Scalability: We can modify the scalability. The size of the network can be decided manually.
- Privacy: It has increased the level of privacy for confidentiality reasons as the businesses required.
- Balanced: It is more balanced as only some user has the access to the transaction which improves the performance of the network.
Disadvantages:
- Security- The number of nodes in this type is limited so chances of manipulation are there. These blockchains are more vulnerable.
- Centralized- Trust building is one of the main disadvantages due to its central nature. Organizations can use this for malpractices.
- Count- Since there are few nodes if nodes go offline the entire system of blockchain can be endangered.
Use Cases: With proper security and maintenance, this blockchain is a great asset to secure information without exposing it to the public eye. Therefore companies use them for internal auditing, voting, and asset management. An example of private blockchains is Hyperledger, Corda.
3. Hybrid Blockchain
It is the mixed content of the private and public blockchain, where some part is controlled by some organization and other makes are made visible as a public blockchain.
- It is a combination of both public and private blockchain.
- Permission-based and permissionless systems are used.
- User access information via smart contracts
- Even a primary entity owns a hybrid blockchain it cannot alter the transaction
Advantages:
- Ecosystem: Most advantageous thing about this blockchain is its hybrid nature. It cannot be hacked as 51% of users don’t have access to the network
- Cost: Transactions are cheap as only a few nodes verify the transaction. All the nodes don’t carry the verification hence less computational cost.
- Architecture: It is highly customizable and still maintains integrity, security, and transparency.
- Operations: It can choose the participants in the blockchain and decide which transaction can be made public.
Disadvantages:
- Efficiency: Not everyone is in the position to implement a hybrid Blockchain. The organization also faces some difficulty in terms of efficiency in maintenance.
- Transparency: There is a possibility that someone can hide information from the user. If someone wants to get access through a hybrid blockchain it depends on the organization whether they will give or not.
- Ecosystem: Due to its closed ecosystem this blockchain lacks the incentives for network participation.
Use Case: It provides a greater solution to the health care industry, government, real estate, and financial companies. It provides a remedy where data is to be accessed publicly but needs to be shielded privately. Examples of Hybrid Blockchain are Ripple network and XRP token.
4. Consortium Blockchain
It is a creative approach that solves the needs of the organization. This blockchain validates the transaction and also initiates or receives transactions.
- Also known as Federated Blockchain.
- This is an innovative method to solve the organization’s needs.
- Some part is public and some part is private.
- In this type, more than one organization manages the blockchain.
Advantages:
- Speed: A limited number of users make verification fast. The high speed makes this more usable for organizations.
- Authority: Multiple organizations can take part and make it decentralized at every level. Decentralized authority, makes it more secure.
- Privacy: The information of the checked blocks is unknown to the public view. but any member belonging to the blockchain can access it.
- Flexible: There is much divergence in the flexibility of the blockchain. Since it is not a very large decision can be taken faster.
Disadvantages:
- Approval: All the members approve the protocol making it less flexible. Since one or more organizations are involved there can be differences in the vision of interest.
- Transparency: It can be hacked if the organization becomes corrupt. Organizations may hide information from the users.
- Vulnerability: If few nodes are getting compromised there is a greater chance of vulnerability in this blockchain
Use Cases: It has high potential in businesses, banks, and other payment processors. Food tracking of the organizations frequently collaborates with their sectors making it a federated solution ideal for their use. Examples of consortium Blockchain are Tendermint and Multichain.
Cryptography and its Types
Cryptography is a technique of securing communication by converting plain text into ciphertext. It involves various algorithms and protocols to ensure data confidentiality, integrity, authentication, and non-repudiation.
What is Cryptography?
Cryptography is a technique of securing information and communications through the use of codes so that only those persons for whom the information is intended can understand and process it. Thus preventing unauthorized access to information. The prefix “crypt” means “hidden” and the suffix “graphy” means “writing”. In Cryptography, the techniques that are used to protect information are obtained from mathematical concepts and a set of rule-based calculations known as algorithms to convert messages in ways that make it hard to decode them. These algorithms are used for cryptographic key generation, digital signing, and verification to protect data privacy, web browsing on the internet and to protect confidential transactions such as credit card and debit card transactions.
Features Of Cryptography
- Confidentiality: Information can only be accessed by the person for whom it is intended and no other person except him can access it.
- Integrity: Information cannot be modified in storage or transition between sender and intended receiver without any addition to information being detected.
- Non-repudiation: The creator/sender of information cannot deny his intention to send information at a later stage.
- Authentication: The identities of the sender and receiver are confirmed. As well destination/origin of the information is confirmed.
- Interoperability: Cryptography allows for secure communication between different systems and platforms.
- Adaptability: Cryptography continuously evolves to stay ahead of security threats and technological advancements.
Types Of Cryptography
1. Symmetric Key Cryptography
It is an encryption system where the sender and receiver of a message use a single common key to encrypt and decrypt messages. Symmetric Key cryptography is faster and simpler but the problem is that the sender and receiver have to somehow exchange keys securely. The most popular symmetric key cryptography systems are Data Encryption Systems (DES) and Advanced Encryption Systems (AES).
-768.png)
Symmetric Key Cryptography
2. Hash Functions
There is no usage of any key in this algorithm. A hash value with a fixed length is calculated as per the plain text which makes it impossible for the contents of plain text to be recovered. Many operating systems use hash functions to encrypt passwords.
3. Asymmetric Key Cryptography
In Asymmetric Key Cryptography, a pair of keys is used to encrypt and decrypt information. A receiver’s public key is used for encryption and a receiver’s private key is used for decryption. Public keys and Private keys are different. Even if the public key is known by everyone the intended receiver can only decode it because he alone knows his private key. The most popular asymmetric key cryptography algorithm is the RSA algorithm.
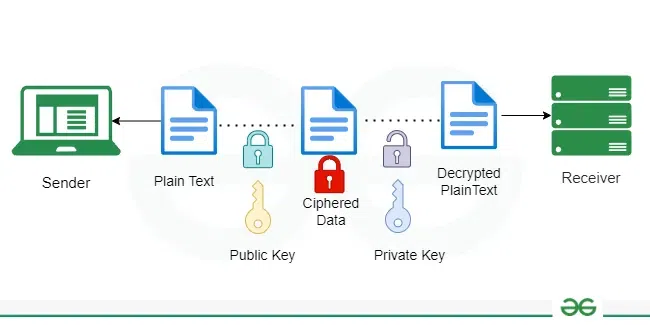
Asymmetric Key Cryptography
Applications of Cryptography
- Computer passwords: Cryptography is widely utilized in computer security, particularly when creating and maintaining passwords. When a user logs in, their password is hashed and compared to the hash that was previously stored. Passwords are hashed and encrypted before being stored. In this technique, the passwords are encrypted so that even if a hacker gains access to the password database, they cannot read the passwords.
- Digital Currencies: To protect transactions and prevent fraud, digital currencies like Bitcoin also use cryptography. Complex algorithms and cryptographic keys are used to safeguard transactions, making it nearly hard to tamper with or forge the transactions.
- Secure web browsing: Online browsing security is provided by the use of cryptography, which shields users from eavesdropping and man-in-the-middle assaults. Public key cryptography is used by the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols to encrypt data sent between the web server and the client, establishing a secure channel for communication.
- Electronic signatures: Electronic signatures serve as the digital equivalent of a handwritten signature and are used to sign documents. Digital signatures are created using cryptography and can be validated using public key cryptography. In many nations, electronic signatures are enforceable by law, and their use is expanding quickly.
- Authentication: Cryptography is used for authentication in many different situations, such as when accessing a bank account, logging into a computer, or using a secure network. Cryptographic methods are employed by authentication protocols to confirm the user’s identity and confirm that they have the required access rights to the resource.
- Cryptocurrencies: Cryptography is heavily used by cryptocurrencies like Bitcoin and Ethereum to protect transactions, thwart fraud, and maintain the network’s integrity. Complex algorithms and cryptographic keys are used to safeguard transactions, making it nearly hard to tamper with or forge the transactions.
- End-to-end Internet Encryption: End-to-end encryption is used to protect two-way communications like video conversations, instant messages, and email. Even if the message is encrypted, it assures that only the intended receivers can read the message. End-to-end encryption is widely used in communication apps like WhatsApp and Signal, and it provides a high level of security and privacy for users.
Types of Cryptography Algorithm
- Advanced Encryption Standard (AES): AES is a popular encryption algorithm which uses the same key for encryption and decryption It is a symmetric block cipher algorithm with block size of 128 bits, 192 bits or 256 bits. AES algorithm is widely regarded as the replacement of DES (Data encryption standard) algorithm
- Data Encryption Standard (DES): DES is an older encryption algorithm that is used to convert 64-bit plaintext data into 48-bit encrypted ciphertext. It uses symmetric keys (which means same key for encryption and decryption). It is kind of old by today’s standard but can be used as a basic building block for learning newer encryption algorithms.
- RSA: RSA is an basic asymmetric cryptographic algorithm which uses two different keys for encryption. The RSA algorithm works on a block cipher concept that converts plain text into cipher text and vice versa.
- Secure Hash Algorithm (SHA): SHA is used to generate unique fixed-length digital fingerprints of input data known as hashes. SHA variations such as SHA-2 and SHA-3 are commonly used to ensure data integrity and authenticity. The tiniest change in input data drastically modifies the hash output, indicating a loss of integrity. Hashing is the process of storing key value pairs with the help of a hash function into a hash table.
Advantages of Cryptography
- Access Control: Cryptography can be used for access control to ensure that only parties with the proper permissions have access to a resource. Only those with the correct decryption key can access the resource thanks to encryption.
- Secure Communication: For secure online communication, cryptography is crucial. It offers secure mechanisms for transmitting private information like passwords, bank account numbers, and other sensitive data over the Internet.
- Protection against attacks: Cryptography aids in the defense against various types of assaults, including replay and man-in-the-middle attacks. It offers strategies for spotting and stopping these assaults.
- Compliance with legal requirements: Cryptography can assist firms in meeting a variety of legal requirements, including data protection and privacy legislation.
How does Secure Hash Algorithm works?
The Secure Hash Algorithm (SHA) was invented by the National Security Agency (NSA) and published in 1993 through the National Institute of Standard and Technology (NIST) as a U.S. Federal Information Processing Standard (FIPS PUB 180).
SHA depends on and shares the similar building blocks as the MD4 algorithm. The design of SHA introduced a new process which develop the 16-word message block input to the compression function to an 80-word block between other things.
The processing of SHA works as follows −
Step 1 − Append padding bits − The original message is padded and its duration is congruent to 448 modulo 512. Padding is continually inserted although the message already has the desired length. Padding includes a single 1 followed by the essential number of 0 bits.
Step 2 − Append length − A 64-bit block considered as an unsigned 64-bit integer (most essential byte first), and defining the length of the original message (before padding in step 1), is added to the message. The complete message's length is a multiple of 512.
Step 3 −Initialize the buffer − The buffer includes five (5) registers of 32 bits each indicated by A, B, C, D, and E. This 160-bit buffer can be used to influence temporary and final outcomes of the compression function. These five registers are initialized to the following 32-bit integers (in hexadecimal notation).
A = 67 45 23 01
B = ef cd ab 89
C = 98 ba dc fe
D = 10 32 54 76
E = c3 d2 e1 f0
The registers A, B, C, and D are actually the same as the four registers used in MD5 algorithm. But in SHA-1, these values are saved in big-endian format, which define that the most essential byte of the word is located in the low-address byte position. Therefore the initialization values (in hexadecimal notation) occurs as follows −
word A = 67 45 23 01
word B = ef cd ab 89
word C = 98 ba dc fe
word D = 10 32 54 76
word E = c3 d2 e1 f0
Step 4 − Process message in 512-bit blocks − The compression function is divided into 20 sequential steps includes four rounds of processing where each round is made up of 20 steps.
The four rounds are structurally same as one another with the only difference that each round need a different Boolean function, which it can define as f1, f2, f3, f4 and one of four multiple additive constants Kt (0 ≤t ≤79) which is based on the step under consideration.
Step 5 − Output − After processing the final 512-bit message block t (considering that the message is divided into t 512-bit blocks), and it can obtain a 160-bit message digest.
Module 2
Working of BlockChain:
How Does a Blockchain Work?
The transaction process in a blockchain can be summarized as follows:
1. Facilitating a transaction: A new transaction enters the blockchain network. All the information that needs to be transmitted is doubly encrypted using public and private keys.
2. Verification of transaction: The transaction is then transmitted to the network of peer-to-peer computers distributed across the world. All the nodes on the network will check for the validity of the transaction like if a sufficient balance is available for carrying out the transaction.
3. Formation of a new block: In a typical blockchain network there are many nodes and many transactions get verified at a time. Once the transaction is verified and declared a legitimate transaction, it will be added to the mempool. All the verified transactions at a particular node form a mempool and such multiple mempools form a block.
4. Consensus Algorithm: The nodes that form a block will try to add the block to the blockchain network to make it permanent. But if every node is allowed to add blocks in this manner then it will disrupt the working of the blockchain network. To solve this problem, the nodes use a consensus mechanism to ensure that every new block that is added to the Blockchain is the only version of the truth that is agreed upon by all the nodes in the Blockchain, and only a valid block is securely attached to the blockchain. The node that is selected to add a block to the blockchain will get a reward and hence we call them “miners”. The consensus algorithm creates a hash code for that block which is required to add the block to the blockchain.
5. Addition of the new block to the blockchain: After the newly created block has got its hash value and is authenticated, now it is ready to be added to the blockchain. In every block, there is a hash value of the previous block and that is how the blocks are cryptographically linked to each other to form a blockchain. A new block gets added to the open end of the blockchain.
6. Transaction complete: As soon as the block is added to the blockchain the transaction is completed and the details of this transaction are permanently stored in the blockchain. Anyone can fetch the details of the transaction and confirm the transaction.
Let’s understand this working of blockchain with the help of an example:
Let’s say Jack and Phil are two nodes on the bitcoin blockchain network who wants to carry out a transaction between them.
Step 1: Facilitating the transaction: Jack wants to send 20 BTC to Phil via the Blockchain network.
Step 2: Verification of transaction: The message for verification will be sent to all the nodes on the network. All the nodes will check the important parameters related to the transaction like Does Jack has sufficient balance i.e. at least 20BTC to perform the transaction. Is Jack a registered node? Is Phil a registered node? After checking the parameters the transaction is verified.
Step 3: Formation of a new block: A number of verified transactions stack up in mempools and get stored in a block. This verified transaction will also get stored in a block.
Step 4: Consensus algorithm: Since here we are talking about bitcoins so the Proof-of-Work consensus algorithm will be used for block verification. In proof-of-work, the system assigns the target hash value to a node, and according to this, it must come up with a hash for the new block. The node has to calculate the hash value for the new block that is less than the target value. If two or more miners mine the same block at the same time, the block with more difficulty is selected. The others are known as stale blocks. Mining usually rewards miners with blockchain currency. In this case, the blockchain currency is bitcoin.
Step 5: Addition of the new block in the blockchain: After the newly created block has got the hash value and authentication through proof-of-work only then it will be added to the network and the transaction will mark as complete. Phil will receive 20 BTC from Jack. The new block will be linked to the open end of the blockchain.
Step 6: Transaction complete: As soon as the block is added to the blockchain, the transaction will take place and 20 BTCs will get transferred from Jack’s wallet to Phil’s wallet. The details of the transaction are permanently secured on the blockchain.
Is Blockchain Secure?
In the most basic way, one can think of a blockchain as a linked list. Each of the next items in the list is dependent on the previous item, except for the first block, also known as the genesis block, which is hardcoded into the blockchain. In the blockchain, each block contains the hash of the previous block’s header and a hash of the transactions in the Merkle tree of the current block. In this way, each block is cryptographically chained to the previous block. Let’s understand with an example what happens when someone attempts to change a transaction or block data in a blockchain network.
- Suppose, there is a chain of 10 blocks, where the 10th block depends on the 9th block, the 9th block depends on the 8th block, and so on.
- In this way, the 10th block depends on all the previous blocks and the genesis block as well.
- If someone tries to change data on the 2nd block, then the attacker will have to change data on all the later blocks as well, otherwise, the blockchain will become invalid since the later blocks depend on the hash value present in the 2nd block and the 2nd block has changed, but not the later blocks.
- Thus, as the blocks are added, immutability increases as changing the block is an expensive operation.
- Also, to add/change a block in a blockchain, a consensus algorithm is used by nodes in the blockchain network. In order to compensate for the change in one block, one must have to recalculate the hash of every block to update the hash value of the block header in the next block. This will involve a lot of time and computational resources.
- In order to succeed with such kind of attack, the hacker has to simultaneously control and change 51% or more copies of the blockchain so that their new copy becomes the majority copy and thus the agreed-upon chain.
- Thus, requiring an immense amount of time, money, and computational resources.
Factors which make blockchain so secure from hackers?
- Byzantine General problem: According to this, if 2/3rd of miners agree to add the block in the chain then only the block will be added. It does’t matter what 1/3rd miners say. This makes blockchain very secure. Byzantine General problem is actually three group of army with their generals attacking on a Byzantine from three sides of it. They mutually decided that if atleast 2 generals agree on attacking the byzantine then only attack will be started because one general may be compromised. On this principle only blockchain works.
- Proof of work: For adding block into the chain, proof of work is needed. miner need to solve tough math calculation to mine the block and this needs huge energy and time consumption. After this also, miners verifies that block is not compromised. That’s why it becomes futile for hackers to try breaching the blockchain.
How blockchain mining works:
Blockchain mining works in various steps from transaction to being added into the chain. These steps are:
- Transaction: Transaction is the transfer of data from one party to another on a blockchain network. After transaction a block is created which is needed to be mined.
- Solve math problem: Miners or group of miners are required to solve a mathematical problem which is to get a particular hash by changing various factors.
- Block solved: Block is mined by the miner by solving the problem.
- Miners verify the validity: Other miners verify that the added block is not malicious. If it is compromised then hackers doesn’t get the reward and ends up wasting time and resources. If the block is normal then the miner who mined gets rewarded.
- Block is added: After the successful steps, block is added to the blockchain.
Blockchain and Distributed Ledger Technology (DLT)
A blockchain is a digital ledger of transactions that are distributed across the entire network of computers (or nodes) on the blockchain. Distributed ledgers use independent nodes to record, share, and synchronize transactions in their respective electronic ledgers instead of keeping them in one centralized server. A blockchain uses several technologies like digital signatures, distributed networks, and encryption/ decryption methods including distributed ledger technology to enable blockchain applications.
Blockchain is one of the types of DLT in which transactions are recorded with an unchangeable cryptographic signature called a hash. That is why distributed ledgers are often called blockchains.
What is Distributed Ledger Technology (DLT)?
Distributed Ledger Technology (DLT) is centered around an encoded and distributed database where records regarding transactions are stored. A distributed ledger is a database that is spread across various computers, nodes, institutions, or countries accessible by multiple people around the globe.
Features:
- Decentralized: It is a decentralized technology and every node will maintain the ledger, and if any data changes happen, the ledger will get updated. The process of updating takes place independently at each node. Even small updates or changes made to the ledger are reflected and the history of that change is sent to all participants in a matter of seconds.
- Immutable: Distributed ledger uses cryptography to create a secure database in which data once stored cannot be altered or changed.
- Append only: Distributed ledgers are append-only in comparison to the traditional database where data can be altered.
- Distributed: In this technology, there is no central server or authority managing the database, which makes the technology transparent. To counter the weaknesses of having one ledger to rule all, So that there is no one authoritative copy and have specific rules around changing them. This would make the system much more transparent and will make it a more decentralized authority. In this process, every node or contributor of the ledger will try to verify the transactions with the various consensus algorithms or voting. the voting or participation of all the nodes depends on the rules of that ledger. In the case of bitcoin, the Proof of Work consensus mechanism is used for the participation of each node.
- Shared: The distributed ledger is not associated with any single entity. It is shared among the nodes on the network where some nodes have a full copy of the ledger while some nodes have only the necessary information that is required to make them functional and efficient.
- Smart Contracts: Distributed ledgers can be programmed to execute smart contracts, which are self-executing contracts with the terms of the agreement between buyer and seller being directly written into lines of code. This allows for transactions to be automated, secure, and transparent.
- Fault Tolerance: Distributed ledgers are highly fault-tolerant because of their decentralized nature. If one node or participant fails, the data remains available on other nodes.
- Transparency: Distributed ledgers are transparent because every participant can see the transactions that occur on the ledger. This transparency helps in creating trust among the participants.
- Efficiency: The distributed nature of ledgers makes them highly efficient. Transactions can be processed and settled in a matter of seconds, making them much faster than traditional methods.
- Security: Distributed ledgers are highly secure because of their cryptographic nature. Every transaction is recorded with a cryptographic signature that ensures that it cannot be altered. This makes the technology highly secure and resistant to fraud.
How DLT Can Replace Traditional Book-Keeping Methods?
Distributed ledger technology has the potential to effectively improve these traditional methods of bookkeeping by updating and modifying fundamental methods of how data is collected, shared, and managed in the ledger. To understand this, traditionally paper-based and conventional electronic ledgers were used to manage data that had a centralized point of control. This types of system require high computing resource and labor to maintain ledgers and also had many points of failure. Points of failure like:
- Mistakes made during data entry.
- Manipulation of data could happen which increases the risk of errors.
- Other participants contributing data to the central ledger will not able to verify the legitimacy of data coming from other sources.
However, DLT allows real-time sharing of data with transparency which gives trust that data in the ledger is up to date and legitimate. Also Distributed Ledger Technology eliminates the single point of failure which prevents data in the ledger from being manipulations and errors. In DLT, there is no need for a central authority to validate transactions here different consensus mechanisms are used to validate transactions which eventually makes this process very fast and real-time. Similarly, DLT can reduce the cost of transactions because of this process.
Types of Distributed Ledger Technology
The Distributed Ledgers can be categorized into three categories:
- Permissioned DLT: Nodes have to take permission from a central authority to access or make any changes in the network. Mostly these types of permissions include identity verification.
- Permissionless DLT: There is no central authority to validate transactions, rather existing nodes are collectively responsible for validating the transactions. Various consensus mechanisms are used to validate transactions based on predefined algorithms. In the case of bitcoin proof of work consensus mechanism is used.
- Hybrid DLT: It is combined with both permissionless and permissioned DLTs and can benefit from both of them.
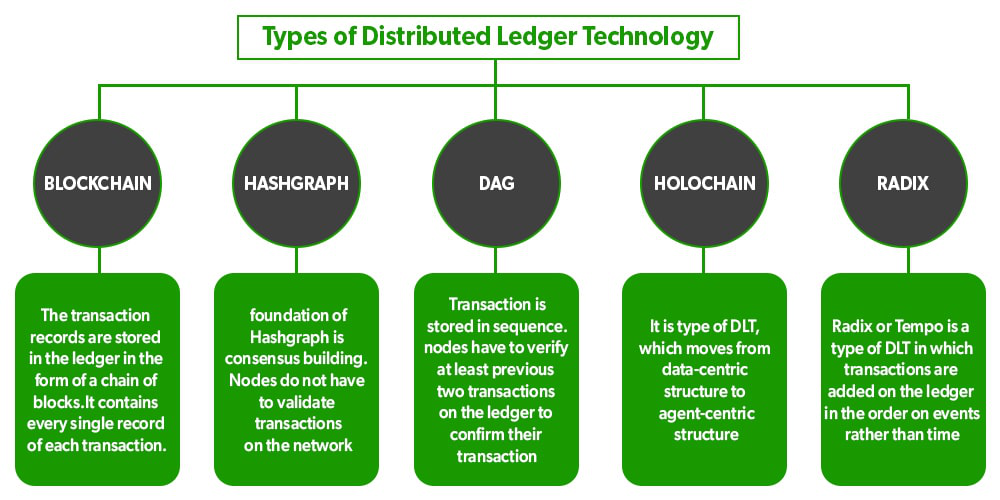
Below are some of the types of DLT:
- Blockchain: In this type of DLT, transactions are stored in the form chain of blocks and each block produces a unique hash that can be used as proof of valid transactions. Each node has a copy of the ledger which makes it more transparent.
- Directed Acyclic Graphs (DAG): This uses a different data structure to organize the data that brings more consensus. In this type of DLT, validation of transactions mostly requires the majority of support from the nodes in the network. Every node on the network has to provide proof of transactions on the ledger and then can initiate transactions. In this nodes have to verify at least two of the previous transactions on the ledger to confirm their transaction.
- Hashgraph: In this type of DLT, records are stored in the form of a directed acyclic graph. It uses a different consensus mechanism, using virtual voting as the form consensus mechanism for gaining network consensus. Hence nodes do not have to validate each transaction on the network.
- Holochain: Holochain is termed as the next level of blockchain by some people because it is much more decentralized than blockchain. It is a type of DLT that simply proposes that each node will run on a chain of its own. Therefore nodes or miners have the freedom to operate autonomously. It basically moves to the agent-centric structure. Here agent means computer, node, miner,etc.
- Tempo or Radix: Tempo uses the method of making a partition of the ledger this is termed sharding and then all the events that happened in the network are ordered properly. Basically, transactions are added to the ledger on basis of the order of events than the timestamp.
Advantages Of Distributed Ledger Technology
- High Transparency: Distributed ledger presents a high level of transparency because all the transaction records are visible to everyone. The addition of data needs to be validated by nodes by using various consensus mechanisms. and if anyone tries to alter or change data in the ledger then it is immediately reflected across all nodes of the network which prevents invalid transactions.
- Decentralized: In a centralized network, there may be a single point of failure and it can disrupt the whole network because of mistakes at the central authority level. But in the case of distributed networks, there is no risk of a single point of failure. because of the decentralized structure trust factor also increases in participating nodes. This decentralized nature of validation reduces the cost of transactions drastically.
- Time Efficient: As this network is decentralized so there is no need for a central authority to validate transactions every time. Hence this time for validation of each transaction reduces drastically. In the case of DLT, transactions can be validated by members of the network itself by using various consensus mechanisms.
- Scalable: Distributed ledger technology is more scalable because many different types of consensus mechanisms can be used to make it more reliant, fast, and updated. Because these many advanced DLT technologies are introduced in the last few years. Such as Holochain, hashgraph are considered to be advanced and more secure versions of Blockchain DLT. Blockchain itself is advanced and secure but DLT provides a way to more advanced technologies.
Uses of Distributed Ledger Technology
Because of all these benefits of distributed ledger technology and this technology has the potential to revolutionize many sectors like Financial, energy, healthcare, governance, supply chain management, real estate, cloud computing, etc.
- Banking: In the banking sector right now transfer of money can be both expensive and time-consuming. Also sending money overseas becomes even more complex due to exchange rates and other hidden fees included. Here DLT can provide a decentralized secure network that will help to reduce the time, complexity, and costs required to transfer money. This decentralized network will eliminate the need for third parties which makes this system more complex and time-consuming.
- Cyber Security: Nowadays cyber security has been emerging as a big threat to governments, enterprises, and individual people also. So it is essential to find an effective solution to secure our data and privacy against unauthorized access. In DLT, all information is authorized and securely encrypted by various cryptographic algorithms. This provides a transparent and secure environment and none of the data can be tempered by any entity.
- Supply chain management: Supply chain is one of the complex structures itself. In this structure, it is hard to trace where the fault happened. So here Distributed ledger technology comes into the picture, Using DLT, you can easily trace the supply chain from the beginning to the end and can easily find out where a mistake or fault has happened. All the data added to the DLT is validated and permanent and can not be altered. This transparency of data enables us to trace from the beginning to the end of the ledger.
- Healthcare: Distributed Ledger eliminates central authority and ensures rapid access to secured and untempered data. Here important medical can be stored securely and no one can change this data, even if someone tries to change it will be reflected everyone immediately. DLT can be used in the insurance sector to trace false claims because of its decentralized system.
- Governance: DLT can be used in the government system to make it transparent among citizens. Many governments have adopted blockchain in the governance system because of the robustness of this system. It can be used as a voting system too. The traditional voting system has many flaws and sometimes it is found that there are many false voting and illegal activities that happen during voting. Online voting systems can be used to vote and with security and fake votes can be easily checked. everyone will have their own identity. So that any person sitting anywhere in the world can cast his vote.
How are Blockchain And Distributed Ledger Different?
In general blockchain and Distributed Ledger Technology are considered as same, but there are some differences between these two technologies. Blockchain can be classified as a type of Distributed Ledger Technology. We can say that Blockchain is a type of DLT, but every Distributed Ledger can not be called a blockchain.
Blockchain is the parent technology of DLT. But the idea behind them is the same. Blockchain technology has the potential to solve many problems in the banking and financial industry. Here, blockchain is the advanced version of Distributed Ledger Technology with many useful functionalities. Developers have many other variants of DLTs in the technology world. However, they do not have the many real-life implementations and applications that blockchain has been able to do.
| Basis | Distributed Ledger | Blockchain Technology |
|---|---|---|
| Block Structure | In DLT, blocks can be organized in different forms. | In Blockchain, blocks are added in the form of a chain. |
| Power of Work | It is more scalable because it does not need the power of a work consensus mechanism for the validation of each transaction. | It is a subset of DLT, the power of the work consensus mechanism adds more functionalities and security. |
| Tokens | It does not require any tokens or digital currency. | In it, tokens must be considered while working with Blockchain. |
| Sequence | It does not require any specific sequence of data. | All blocks are arranged in a particular series. |
| Trustability | Trust among participating nodes is high. | Trust among participating nodes is less than DLT. Decision-making powers can be on one hand because everyone can mine. |
Advantages of Using Distributed Ledger Technology In Blockchain
- Security: All records of every transaction are securely encrypted. Once the transaction is validated, it is completely secure and no one can update or change it. It is a permanent process.
- Decentralization: All network members or nodes have a copy of the ledger for complete transparency. A decentralized private distributed network improves the reliability of the system and gives assurance of continuous operations without any interruption. It gives control of information and data in the hand of the user.
- Anonymity: The identity of each participant is anonymous and does not possibly reveal their identity.
- Immutable: Any validated transactions can not be changed as they are irreversible.
- Transparency: Distributed technologies offer a high level of transparency. Which is necessary for the sectors like finance, medical science, banking, etc.
- Speed: Distributed Ledger Technology can handle large transactions faster than traditional methods.
- Smart Contracts: Distributed Ledger Technology supports smart contracts which are self-executing contracts with the terms of the agreement between buyer and seller being directly written into lines of code. Smart contracts reduce the need for intermediaries and offer transparency and automation in the execution of the contract terms.
- Lower Costs: Distributed Ledger Technology eliminates intermediaries and reduces the costs associated with intermediaries, which makes the system more cost-effective.
- Improved Efficiency: Distributed Ledger Technology reduces the time and costs associated with traditional transaction methods. It offers faster settlement times, reduced paperwork, and increased efficiency.
- Auditing: Distributed Ledger Technology makes auditing easier as every transaction is recorded and the ledger cannot be altered. This improves the transparency and accuracy of financial audits.
- Resilience: Distributed Ledger Technology is more resilient than traditional databases as it is spread across multiple nodes. This means that even if one node goes down, the network can still function as the rest of the nodes can continue to validate transactions.
- Traceability: Distributed Ledger Technology offers complete traceability of assets, from their creation to their current ownership. This improves accountability and reduces the risks of fraud and theft.
Disadvantages Of Distributed Ledger Technology
- 51% Attack: The 51% attack is a bit concerning part of this distributed ledger technology that is to be checked routinely.
- Costs of Transaction: The connected nodes are expected to validate the transaction of a given Distributed Ledger Technology which gives high transaction cost as the other nodes are paid incentives to validate the transaction.
- Slow Transaction Speed: The major disadvantage of this DLT is the slow speed of transactions as multiple nodes are attached to this network and it takes time to validate the transaction by all the other nodes.
- Scalability Issues: Due to low speed and high transaction costs DLT faces very difficulties to expand on a large scale.
- Lack of Regulation: As DLT is a decentralized technology, it operates outside the control of any centralized authority which can lead to a lack of regulation, making it difficult to hold accountable any wrongdoings or fraudulent activities on the network.
- Energy Consumption: Distributed Ledger Technology requires a significant amount of energy to maintain the network and validate transactions, especially in the case of Proof of Work consensus mechanisms, which can lead to a negative impact on the environment.
- Complexity: Implementing and managing Distributed Ledger Technology can be complex and requires a high level of technical expertise, which can be a barrier to entry for many organizations and individuals.
- Privacy Concerns: While the anonymity of participants on the network is considered an advantage, it can also be a disadvantage as it can lead to privacy concerns and illicit activities on the network.
- Lack of Interoperability: Different Distributed Ledger Technologies may use different protocols, which can lead to interoperability issues, making it difficult for different networks to communicate and transact with each other.
Blocks are the basic constructs of blockchain. Each block contains a set of transactions, metadata, and mining information.
Block in a Blockchain–
- Blockchain is a linear chain of blocks.
- Each block contains a set of transactions and other essential details.
- Blocks are linearly connected and cryptographically secured.
- Each block header contains the previous block hash, current block hash, nonce, Merkle root, and other details.
- All blocks are connected linearly by carrying the hash of the previous block.
- The previous block hash is used to compute the current block hash.
- The first block with no previous block hash is called “Genesis Block.”
- For adding a new block to the network, the blockchain follows consensus mechanisms like proof of work (PoW), proof of stake (PoS), etc.
It’s the sequence number of the block in the chain of blocks. Block Height: 1 is the genesis block (first block in the network).
Block Size –
It’s a 4-bytes or 32-bit field that contains the size of the block. It adds size in Bytes. Ex – Block Size: 216 Bytes.
Block Reward –
This field contains the amount rewarded to the miner for adding a block of transactions.
Tx Count –
The transaction counter shows the number of transactions contained by the block. The field has a maximum size of 9 bytes.
Block Header –
The Block header is an 80-Byte field that contains the metadata – the data about the block.
Let’s briefly discuss the 6 components of the Block Header.
- Time – It’s the digitally recorded moment of time when the block has been mined. It is used to validate the transactions.
- Version – It’s a 4-bytes field representing the version number of the protocol used. Usually, for bitcoin, it’s ‘0x1’.
- Previous Block Hash – It’s a 32-bytes field that contains a 256-bits hash (created by SHA-256 cryptographic hashing) of the previous block. This helps to create a linear chain of blocks.
- Bits – It’s a 4-bytes field that tells the complexity to add the block. It’s also known as “difficulty bits.” According to PoW, the block hash should be less than the difficulty level.
- Nonce – It’s a 4-bytes field that contains a 32-bit number. These are the only changeable element in a block of transactions. In PoW, miners alter nonce until they find the right block hash.
- Merkle Root – A 32-bytes field containing a 256-bit root hash. It’s constructed hierarchically combining hashes of the individual transactions in a block.
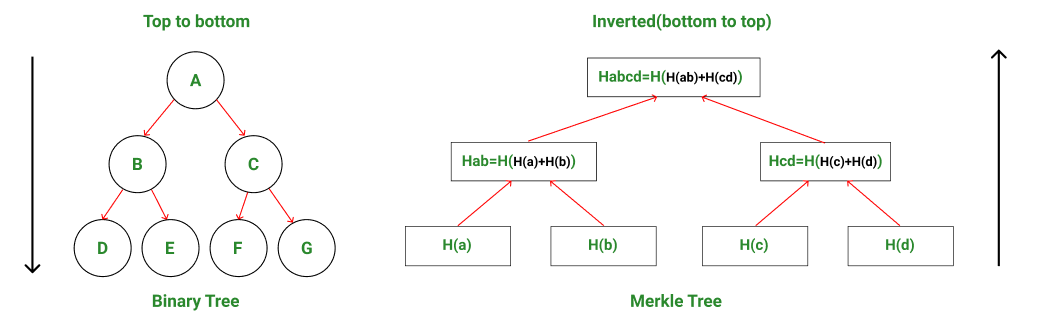
How Do Merkle Trees Work?
- A Merkle tree is constructed from the leaf nodes level all the way up to the Merkle root level by grouping nodes in pairs and calculating the hash of each pair of nodes in that particular level. This hash value is propagated to the next level. This is a bottom-to-up type of construction where the hash values are flowing from down to up direction.
- Hence, by comparing the Merkle tree structure to a regular binary tree data structure, one can observe that Merkle trees are actually inverted down.
Understanding Double Spending
Although Blockchain is secured, still it has some loopholes. Hackers or malicious users take advantage of these loopholes to perform their activities.
- Double spending means the expenditure of the same digital currency twice or more to avail the multiple services. It is a technical flaw that allows users to duplicate money.
- Since digital currencies are nothing but files, a malicious user can create multiple copies of the same currency file and can use it in multiple places.
- This issue can also occur if there is an alteration in the network or copies of the currency are only used and not the original one.
- There are also double spends that allow hackers to reverse transactions so that transaction happens two times.
- By doing this, the user loses money two times one for the fake block created by the hacker and for the original block as well.
- The hacker gets incentives as well for the fake blocks that have been mined and confirmed.
How Does Double Spending Happen?
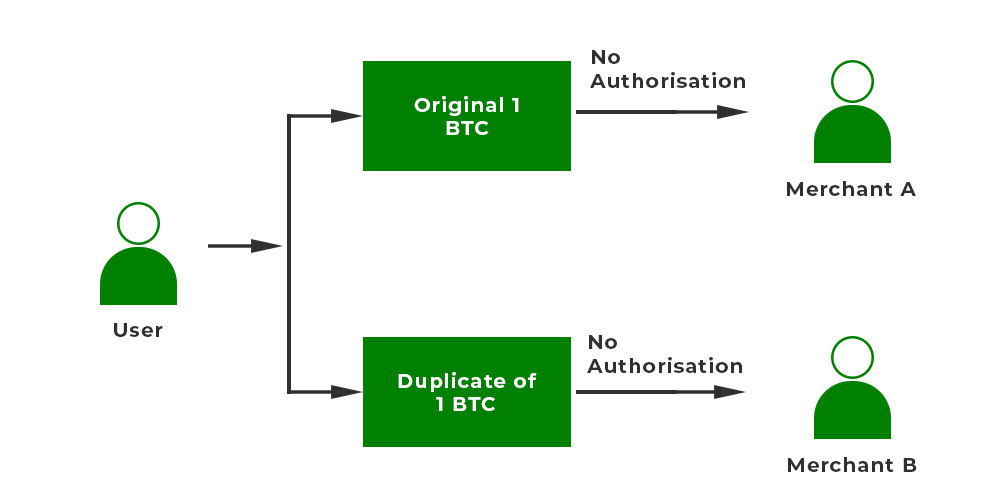
Double spending can never arise physically. It can happen in online transactions. This mostly occurs when there is no authority to verify the transaction. It can also happen if the user’s wallet is not secured. Suppose a user wants to avail of services from Merchant ‘A’ and Merchant ‘B’.
- The user first made a digital transaction with Merchant ‘A’.
- The copy of the cryptocurrency is stored on the user’s computer.
- So the user uses the same cryptocurrency to pay Merchant ‘B’
- Now both the merchants have the illusion that the money has been credited since the transactions were not confirmed by the miners.
This is the case of double spending.

Example: Suppose a user has 1 BTC. He/She wants to avail of services from merchant A and merchant B. The user creates multiple copies of the same BTC and stores it. The user first sends the original BTC to Merchant A and gets the service. Simultaneously, the user sends the copied version of 1 BTC to Merchant B. Since the second transaction was not confirmed by other miners, the merchant accepts the bitcoin and sends the service. But the cryptocurrency that was sent is invalid. This is the case of Double Spending.
Types Of Double Spending Attacks
There are different types of Double Spending attacks:
- Finney Attack: Finney Attack is a type of Double spending Attack. In this, a merchant accepts an unauthorized transaction. The original block is eclipsed by the hacker using an eclipse attack. The transaction is performed on an unauthorized one. After that, the real block shows up and again the transaction is done automatically for the real block. Thus the merchant loses money two times.
- Race attack: is an attack in which there is a ‘race’ between two transactions. The attacker sends the same money using different machines to two different merchants. The merchants send their goods but transactions get invalid.
- 51% Attack: This type of attack is prevalent in small blockchains. Hackers usually take over 51% of the mining power of blockchain and therefore can do anything of their own will.
How Bitcoin Handles Double Spending?
Bitcoin is one of the most popular blockchains. To combat Double spending it uses some security measures. There are two types of examples of double spending in BTC.
- The first case is making duplicates of the same bitcoin and sending it to multiple users.
- The second case is performing the transaction and reversing the already sent transaction after getting the service.
To tackle these double-spending issues, some security measures are taken. They are:
- Validation: Validation of transactions by a maximum number of nodes in the network. Once a block is created, it is added to a list of pending transactions. Users send validation for the block. If the verifications are done then only the block is added to the blockchain.
- Timestamp: The confirmed transactions are timestamped, therefore they are irreversible. If a transaction is involved with a bitcoin it is verified and done. But in the future, if other transactions are made with the same bitcoin, the transactions will be canceled.
- Block Confirmations: Merchants get block confirmations so that they are assured that there was no case of double spending. In bitcoin, a minimum of 6 confirmations are done.
- Saving copies: A copy of each transaction is kept at each node so in case of network failure the whole network does not go down.
These security features have reduced double spending to a large extent. Let us discuss a detailed example of how bitcoin handles double-spending.
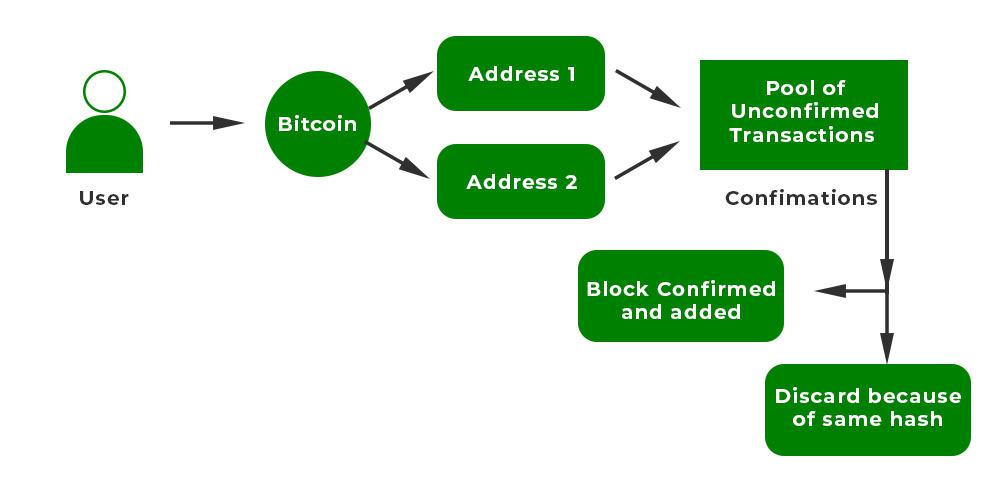
- A user wants to spend 2 BTC. He/She can create multiple copies of the same cryptocurrency.
- The user can send the same cryptocurrency to two different addresses say ‘Bob’ and ‘Alice’.
- Both of these transactions are sent to the pool of unconfirmed transactions.
- The first transaction T1 would be approved via the confirmation mechanism.
- The confirmation mechanism states that a minimum of six confirmations by miners should be done for block validation. The block is added to the network.
- However, the second transaction T2 didn’t get sufficient confirmation so it would be recognized as invalid by the confirmation process. The block with the highest number of confirmations is accepted and the other one is rejected. So transaction T1 is valid, and Alice received the bitcoin.
Solutions To Prevent Double Spending
Double Spending can be prevented using two approaches: Centralized and Decentralized
- Centralized Approach: In this case, a secured third party is employed to verify the transactions. The third-party can track each of the user’s balances. Suppose a user makes a transaction. The third-party identifies the transaction with a unique identity. Then it verifies the transaction and allows the transaction. The problem is that suppose we want to make transactions with other countries where a third party is not required. So in such cases, decentralized systems come into play. another drawback is if the whole system fails, the users cannot have access.
- Decentralized Approach: This approach is used by Bitcoin. In this, there is no involvement of central authority. Each transaction is verified using powerful algorithms. The decentralized approach proved to be more secure than the centralized approach. Protocols are established and each protocol does its job at each step. Therefore this also promotes transparency.
How to Combat Double Spending?
Double spending has been minimized to a large extent as companies are using many security features. But we as users also have some responsibility so that such attacks don’t happen.
- Any user should wait for a minimum of six confirmations of the transaction before performing another transaction. In the blockchain, more the confirmations by different users, lesser will be double spending attacks.
- Users should keep their hardware resources safe so that hackers do not misuse them for their own purposes. Often hackers target the hardware part because the hardware is costly. If they somehow steal the hardware, they can roll back any transaction or alter information.
- Users should delete spam mails and avoid phishing to avoid unnecessary malware attacks Phishing is a very common attack by hackers as hackers target login credentials.
- Software should be updated regularly with the latest antivirus installed. If the software is not up to date then the bugs present can cause major damage.
How Successful Double Spending is Administered?
With the increasing dependency on the blockchain, double spending attacks have also become a major problem. Many companies have adopted security features.
- Features like confirmation of the transaction by the nodes have been adopted. A minimum of six confirmations is required to approve the transaction.
- The blocks once created are immutable. They are made irreversible so that no transaction is reverted back.
- The network’s distributed ledger of transactions autonomously records each transaction. Each node has a copy of all transactions that are being done in the network.
- Verification of each transaction’s authenticity is done by Blockchain protocols to prevent double-spending. The concept of hashing is adopted. Here each block has a unique hash.
Disadvantages of Blockchain Concerning Double Spending
There are many disadvantages of blockchain concerning Double Spending:
- Control of the blockchain: The biggest disadvantage is if the hackers manage to take control of 51% computation power, they can do any transaction of their own will and can steal other users’ money. Therefore there is a threat to security as millions and millions of money are involved in transactions.
- Alteration of information: Transaction information can also be altered by hackers. They can mine blocks and hide the original blocks using attacks like Eclipse attack, Finney Attack, etc.
- No authority: The third major problem is no central authority is present to verify the transactions. But these problems will be eliminated if companies take proper security measures and users are also aware of the measures.
Blockchain transactions involve transferring digital assets or information within a blockchain network. They are recorded and stored in blocks, creating an immutable and transparent ledger.
Blockchain transactions offer security, transparency, and trust without intermediaries such as banks using cryptographic algorithms and consensus mechanisms.
Understanding the intricacies of blockchain transactions is crucial, especially for those seeking blockchain developer certification.
How do blockchain transactions work?
The transaction flow in blockchain involves a decentralised and secure process whereby transactions are verified and recorded on the blockchain network.
Blockchain transactions undergo verification by network nodes, and valid transactions are added to blocks through a consensus mechanism such as Proof-of-Work (PoW) or Proof-of-Stake (PoS). Miners then validate the blocks by solving puzzles or staking assets.
Once validated, transactions are recorded on the distributed ledger, ensuring transparency and immutability. It removes reliance on intermediaries and offers a validated approach to digital transactions.
Key components of a blockchain transaction
Understanding the transaction flow in blockchain involves vital components that ensure integrity, security, and transparency. These key components are discussed below:
- Sender: Initiates transactions with a valid wallet address
- Recipient: Receives transactions with a valid wallet address
- Transaction Data: Securely stores sender and recipient addresses, the amount transferred, and relevant information
- Transaction ID: Unique identifier generated for locating and verifying the transaction
- Miners: Computers that verify and add transactions, rewarded with cryptocurrency
- Consensus Mechanism: Protocol ensuring agreement on transaction order and blockchain state
- Block: Container bundling verified transactions in the blockchain's chronological chain
- Transaction Fees: Incentives for miners vary based on network congestion and priority
- Public and Private Keys: Cryptography for transaction security, with public keys verifying signatures
- Immutable Ledger: Transactions become permanent parts of the unalterable blockchain ledger
- Signature: Cryptographic hash verifying the authenticity and preventing tampering
Types of blockchain transactions
Some of the most common types of blockchain transactions include:
- Smart Contract Transactions: This type of blockchain transaction involves self-executing agreements written in code, enabling automated actions without intermediaries and ensuring secure and transparent execution of contractual obligations.
- Cryptocurrency Transactions: These transactions involve the exchange of digital currencies such as Bitcoin and Ethereum, providing secure and transparent sending, receiving, and storage of digital assets.
- Decentralised Finance (DeFi) Transactions: DeFi transactions leverage blockchain for various financial activities without traditional intermediaries, with Ethereum and Bitcoin being popularly used.
- Non-Fungible Token (NFT) Transactions: NFT transactions enable the creation, ownership, and trading of unique digital assets across industries such as art, music, gaming, and collectables, revolutionising ownership and empowering creators and collectors.
Understanding transaction fees
Transaction fees are an essential part of the blockchain transaction process, requiring users to pay fees that incentivise miners or validators to include their transactions in the blockchain.
These fees maintain network security and efficiency by preventing congestion in the transaction process in blockchain and compensating those involved in network maintenance.
Common transaction errors and how to avoid them
Here are some blockchain transaction errors and ways to avoid them:
- Wrong recipient address error: Double-check the recipient address to avoid sending funds to the wrong person
- Insufficient funds error: Ensure sufficient funds are in your wallet before executing a transaction
- Network congestion error: Monitor network status and adjust gas fees during high congestion periods
- Smart contract errors: Thoroughly review smart contract code and validate input parameters
- Transaction rejection error: Ensure compliance with transaction requirements and avoid conflicts with existing transactions
- Pending transactions: Attempt to cancel and resend pending transactions, but once added to a block, they cannot be cancelled.
Understanding a Timestamp in Blockchain
A Timestamp refers to a small piece of data stored in every block in a Blockchain as a unique serial. This data ascertains the moment the block mining has occurred and undergone validation by the Blockchain network. Interestingly, a timestamp dates back to its initial usage in historical times when people explored ways to track and authenticate documents.
Timestamps can be understood as writing anything on a Blockchain and then being assigned a time signature containing a particular date corresponding to its parent block. This timestamp containing the data happens to be fixed or immutable, proving its authenticity and transparency.
A primitive example of the first use of timestamping is the postal stamp, the so-called ‘predecessor’ to a timestamp. Back in the 17th century, people attempted to claim possession of important documents, including scientists who attempted to prove possession and ownership over their innovative findings. The scientists would post letters to themselves, for instance, how a scientist and polymath, Robert Hooke, had an anagram published in the late 1600s to prove his discovery of Hooke’s Law.
The advent of computers allowed people to witness one of the first actual executions of timestamping. Although these techniques were not secure enough because they required the presence of a centralised infrastructure, and incidents of data manipulation began consequentially due to this lack. One means of resolving this concern was through decentralisation, which Blockchain networks bring into the picture regarding their practical applications.
Now a timestamp, also known as a ‘temporal parameter’, is based on an immediate adjustment utilising the timestamps’ median, which all existing network nodes have returned. Owing to the reason for its decentralised form, the network nodes are to be kept as well-synchronised as possible. It is also to be noted that the block timestamps are not fixed because they are not necessarily in order.
Benefits of a Timestamp in a Blockchain
Blockchain-based Timestamping offers a decentralized and secure means of keeping track of the manufacturing process. It is to be noted that a timestamp does not have any legal value of its own, as the only valuable part of it is its time signature. Any data entered into a Blockchain becomes legally valid the instant it has been uploaded in a particular manner.
Additionally, timestamps are very important for maintenance. This means a company can track the work on the Blockchain network if it owns any equipment. The company that produces said equipment can observe if and how the maintenance work was carried out, presenting substantial evidence of the event occurrences.
Below is a list of reasons why Blockchain-based timestamping is of benefit:
1) Blockchain Timestamping is, in fact, more secure and trustworthy because it is not possible to remove or change after it has been published to the ledger, making it all the more trustworthy and secure as a result.
2) There is little possibility of meddling by any party because of the decentralised nature of Blockchain.
3) A Blockchain network’s transparency characteristic allows the timestamps to be viewed with transparency as needed.
4) The contrast between traditional and Blockchain-based timestamping illustrates the benefit of timestamping in a Blockchain network. For example, if a company uses a centralised server to track its manufacturing process, the probability of data loss, corruption, or manipulation rises. As a result, this leads to mistrust in the timestamp.
Blockchain networks keep these potential concerns to a down-low by keeping the data encrypted and completely secure right at the source, such that the data cannot be altered or tampered with. This procedure and practice build trust, a crucial aspect of any business workflow, hence why timestamping is worth adopting.
It must also be noted that in case of documentation, the document itself is invisible on the Blockchain. Additionally, hashing is a one-way process where both the signed and unsigned versions of the document will generate different hash values. Once the hash of signed document is entered into the Blockchain, it keeps the document data hidden from those having access to the Blockchain. Although it only allows them to make a note of the hash value for the sake of verifying the document’s authenticity.
Blockchain – Chaining Blocks
Blockchain is the backbone Technology of Digital CryptoCurrency BitCoin. In its most basic definition, blockchain records how a digital asset has been accumulated in a distributed, decentralized fashion. They are designed to prevent data modification, making them an ideal disruptor for industries including payments, cybersecurity, agriculture, and healthcare. Blocks are records linked together by cryptography in a blockchain. In addition to a cryptographic hash of the previous block and the timestamp, each block contains transaction data.
This chain of blocks is what is referred to as a truly distributed ledger, as it is made up of the blocks created by various miners. There are some basic terminologies in blockchain like:
- Block: In a Blockchain, a block represents the ‘present’ and contains information about the past and future of the network.
- Hash: Hash functions are used in Blockchains to secure encrypted demands that are required for a blockchain to work.
Block Chaining
The records which are stored within blocks are immutable and verifiable. Now, let’s take a look at some records which are stored in a blockchain. It can be noticed from the diagram that records have been split into a number of different blocks-
In order to ensure a sequencing of the blocks, these are in fact, chained together, and it is a mechanism of this chaining that ensures not only an ordering of the blocks but also the immutability and verifiability of the records within them.
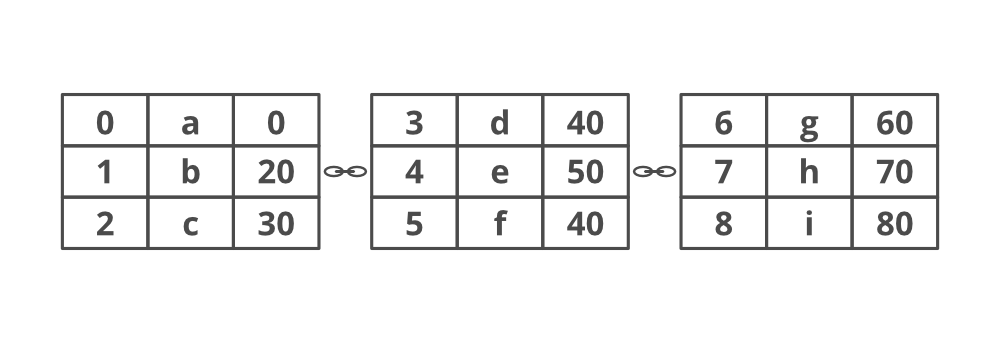
Features of Chaining Blocks:
- There is a cryptography link between adjacent chains.
- Each block in a blockchain includes a cryptography hash of the previous block.
- It also includes the timestamp of the block (when the block was added to the Blockchain). And in the case of Ethereum, it includes all the Transaction data.
- If any individual Transaction which makes up a block has been modified then the hash of that block will be very different from what it was previously. In this way, the cryptographic Link between adjacent blocks will be broken.
- Because of the cryptographic link, any transaction data that has been written into the blockchain cannot be modified after the fact.
- Any node can try to verify the entire blockchain by producing a hash of the very first block and then making sure that those hash contents are present in the second block and the whole process keeps repeating until all the blocks have been verified.
What Happens When Transaction Content Changes?
If there is a need to change the contents of one transaction, in one of the previous blocks in the blockchain, then just re-compute the hash for that block and after that, include that modified block hash in the next block as well. For the next block, if the hash of the previous block has changed then its own hash block will be different, so the hash for that block will also need to be recomputed. In fact, if there is a requirement to change any of the previous transactions written to the blockchain, then it is required to recompute the hash for every single block. and this is something that is not trivial because you will have to reach a consensus among all the nodes which participate in the Blockchain network. Each and every transaction in the Blockchain is both verifiable and immutable or permanent.
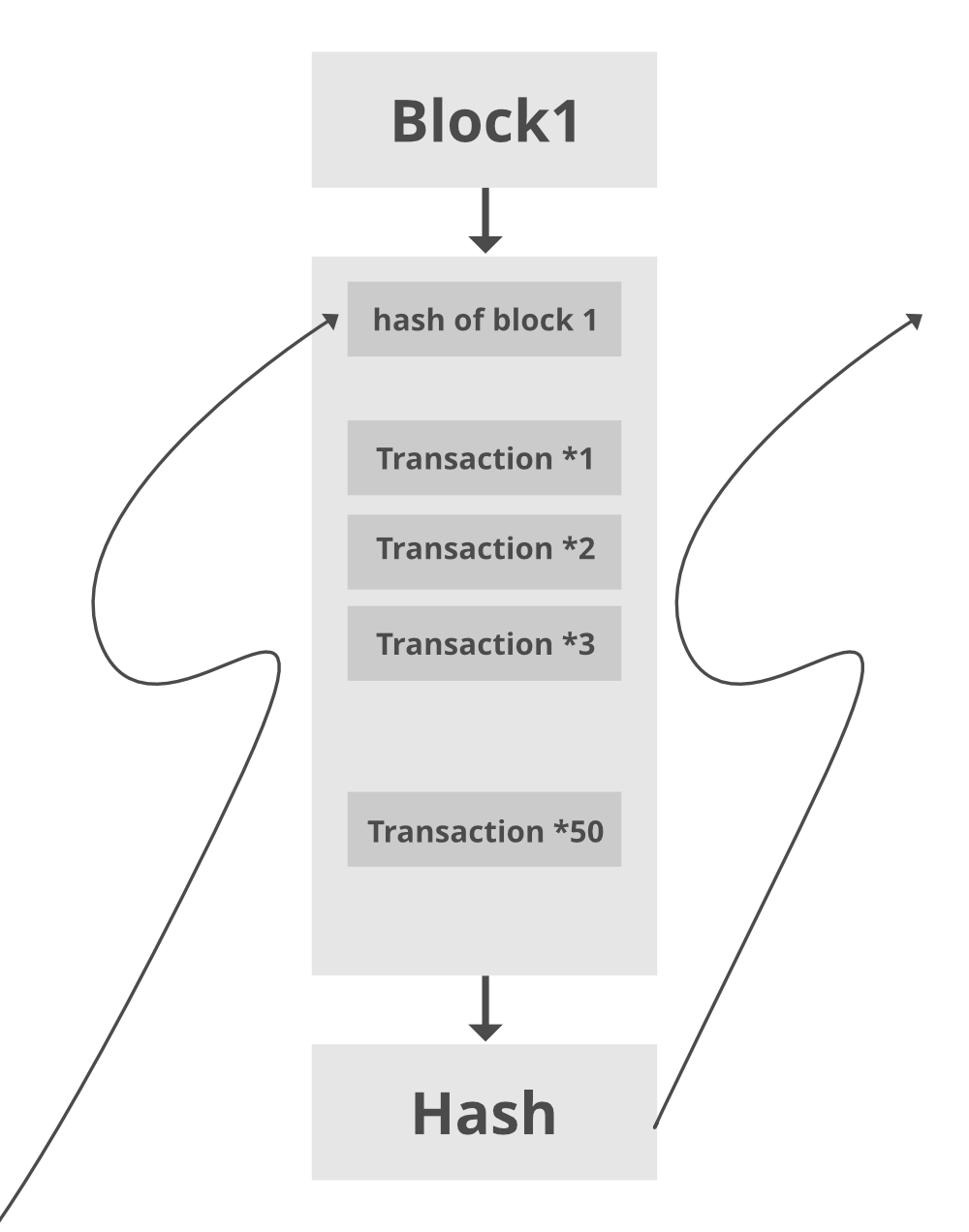
Each block in the blockchain contains multiple transactions and the hash of the previous block is added to the current block when making a chain of blocks.
A hash function is a mathematical function that takes an input string of any length and converts it to a fixed-length output string. The fixed-length output is known as the hash value. To be cryptographically secure and useful, a hash function should have the following properties:
- Collision resistant: Give two messages m1 and m2, it is difficult to find a hash value such that hash(k, m1) = hash(k, m2) where k is the key value.
- Preimage resistance: Given a hash value h, it is difficult to find a message m such that h = hash(k, m).
- Second preimage resistance: Given a message m1, it is difficult to find another message m2 such that hash(k, m1) = hash(k, m2).
- Large output space: The only way to find a hash collision is via a brute force search, which requires checking as many inputs as the hash function has possible outputs.
- Deterministic: A hash function must be deterministic, which means that for any given input a hash function must always give the same result.
- Avalanche Effect: This means for a small change in the input, the output will change significantly.
- Puzzle Friendliness: This means even if one gets to know the first 200 bytes, one cannot guess or determine the next 56 bytes.
- Fixed-length Mapping: For any input of fixed length, the hash function will always generate the output of the same length.
How do Hash Functions work?
A hash function takes an input string (numbers, alphabets, media files) of any length and transforms it into a fixed length. The fixed bit length can vary (like 32-bit or 64-bit or 128-bit or 256-bit) depending on the hash function which is being used. The fixed-length output is called a hash. This hash is also the cryptographic byproduct of a hash algorithm.
The below diagram shows how hashes work.
The hash algorithm has certain unique properties:
- It produces a unique output (or hash).
- It is a one-way function.
The basic steps of the process are as follows:
1. Input is processed by the hashing algorithm
The process of hashing begins with the input, or the data that needs to be hashed. This data can be any kind of information, such as a string of text, a file, or a block of transactions in a blockchain. The input is then passed through the hashing algorithm.
The algorithm applies a set of mathematical rules and operations to the input, such as mathematical transformations, bitwise operations, and logical operations
2. A hash output serves as a digital footprint of the input
The output of the hashing algorithm is the hash, which serves as a digital fingerprint of the input. This hash is a unique representation of the input and typically a string of characters, such as a hexadecimal number, that is a fixed size, depending on the algorithm used.
The key feature of a hashing algorithm is that it is a one-way function, meaning that it is very difficult to determine the original input from the hash. This makes it difficult for someone to alter the contents of a block without being detected, since any changes to the block will result in a different hash.
3. The hash is stored in the block and serves as a digital signature
It is stored in the block along with the data, and it serves as a digital signature that proves the integrity of the data. When the data is needed in the future, the hash can be recalculated, and if it matches the stored hash, it is confirmed that the data has not been tampered with.
Types of Cryptographic Hash Functions
There are several different classes of hash functions. Some of the popular classes are:
1. RACE Integrity Primitives Evaluation Message Digest (RIPEMD): This set includes RIPEMD, RIPEMD-128, RIPEMD-160, RIPEMD-256, RIPEMD-320.
- Out of these RIPEMD-160 is the most common.
- The original RIPEMD-128 is based on the design principles used in MD4.
- The RIPEMD-256 and 320 have fewer chances of the accidental collision but do not have higher levels of security as compared to RIPEMD-128 and RIPEMD-160.
2. Message-Digest Algorithm: This family comprises hash functions MD2, MD4, MD5, and MD6.
- MD5 is the most widely used cryptographic hash function.
- It is used to generate a 128-bit digest from a 512-bit string broken down into 16 words composed of 32 bits each.
- Ronald Rivest designed this algorithm in 1991 to use for digital signature verification.
- These are no longer considered cryptographically secure methods and should not be used for cryptographic authentication.
3. BLAKE2: It was announced on December 21, 2012.BLAKE2 is a cryptographic hash function based on BLAKE, designed with the aim to replace MD5 and SHA-1 algorithms in applications requiring high performance in software. It provides better security than SHA-2 and is similar to that of SHS-3. It provides the following features:
- It provides immunity to length extensions.
- It removes the addition of constants to message words.
- It simplifies padding and reduces the number of rounds from 16 to 12.
4. BLAKE3: It was announced on January 9, 2020. BLAKE3 is a cryptographic function based on Bao and BLAKE2. It is a few times faster than BLAKE2. This algorithm provides many features like parallelism, XOF, KDF, etc.
5. Whirlpool: It is a cryptographic hash function, first described in 2000. It is a modified version of the Advanced Encryption Standard (AES). Whirlpool produces a hash of 512 bits.
6. Secure Hashing Algorithm: The family of SHA comprises four SHA algorithms: SHA-0, SHA-1, SHA-2, and SHA-3.
- SHA-0 is a 160-bit hash function that was published by the National Institute of Standards and Technology in 1993.
- SHA-1 was designed in 1995 to correct the weaknesses of SHA-0. In 2005, a method was found to uncover collisions in the SHA-1 algorithm due to which long-term employability became doubtful.
- SHA-2 has the following SHA variants, SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256. It is a stronger hash function and it still follows the design of SHA-1.
- In 2012, the Keccak algorithm was chosen as the new SHA-3 standard.
- SHA-256 is the most famous of all cryptographic hash functions because it’s used extensively in blockchain technology. The SHA-256 Hashing algorithm was developed by the National Security Agency (NSA) in 2001.
Proof of Stake (PoS) in Blockchain
Proof of Stake (PoS) is a type of algorithm which aims to achieve distributed consensus in a Blockchain. This way to achieve consensus was first suggested by Quantum Mechanic here and later Sunny King and his peer wrote a paper on it. This led to Proof-of-Stake (PoS) based Peercoin.
- Coin-age based selection:The algorithm tracks the time every validator candidate node stays a validator. The older the node becomes, the higher the chances of it becoming the new validator.
- Random Block selection:The validator is chosen with a combination of ‘lowest hash value’ and ‘highest stake’. The node having the best weighted-combination of these becomes the new validator.
A typical PoS based mechanism workflow:
- Nodes make transactions. The PoS algorithm puts all these transactions in a pool.
- All the nodes contending to become validator for the next block raise a stake. This stake is combined with other factors like ‘coin-age’ or ‘randomized block selection’ to select the validator.
- The validator verifies all the transactions and publishes the block. His stake still remains locked and the forging reward is also not granted yet. This is so that the nodes on the network can ‘OK’ the new block.
- If the block is ‘OK’-ed, the validator gets the stake back and the reward too. If the algorithm is using a coin-age based mechanism to select validators, the validator for the current block’s has its coin-age reset to 0. This puts him in a low-priority for the next validator election.
- If the block is not verified by other nodes on the network, the validator loses its stake and is marked as ‘bad’ by the algorithm. The process again starts from step 1 to forge the new block.
Features:
- Fixed coins in existence:There is only a finite number of coins that always circulate in the network. There is no existence of bringing new coins into existence(as in by mining in case of bitcoin and other PoW based systems). Note that the network starts with a finite number of coins or ‘initially starts with PoW, then shifts to PoS’ in some cases. This initiation with PoW is meant to bring coins/cryptocurrency in the network.
- Transaction fee as reward to minters/forgers:Every transaction is charged some amount of fee. This is accumulated and given to the entity who forges the new block. Note that if the forged block is found fraudulent, the transaction fee is not rewarded. Moreover, the stake of the validator is also lost(which is also known as slashing).
- Impracticality of the 51% attack:To conduct a 51% attack, the attacker will have to own 51% of the total cryptocurrency in the network which is quite expensive. This deems doing the attack too tedious, expensive and not so profitable. There will occur problems when amassing such a share of total cryptocurrency as there might not be so much currency to buy, also that buying more and more coins/value will become more expensive. Also validating wrong transactions will cause the validator to lose its stake, thereby being reward-negative.
Advantages of PoS:
- Energy-efficient:As all the nodes are not competing against each other to attach a new block to the blockchain, energy is saved. Also, no problem has to be solved( as in case of Proof-of-Work system) thus saving the energy.
- Decentralization:In blockchains like Bitcoin(Proof of Work system to achieve distributed consensus), an extra incentive of exponential rewards are in place to join a mining pool leading to a more centralized nature of blockchain. In the case of a Proof-of-Stake based system(like Peercoin), rewards are proportional(linear) to the amount of stake. So, it provides absolutely no extra edge to join a mining pool; thus promoting decentralization.
- Security:A person attempting to attack a network will have to own 51% of the stakes(pretty expensive). This leads to a secure network.
Weakness of a PoS mechanism:
- Large stake validators:If a group of validator candidates combine and own a significant share of total cryptocurrency, they will have more chances of becoming validators. Increased chances lead to increased selections, which lead to more and more forging reward earning, which lead to owning a huge currency share. This can cause the network to become centralized over time.
- New technology:PoS is still relatively new. Research is ongoing to find flaws, fix them and making it viable for a live network with actual currency transactions.
- The ‘Nothing at Stake’ problem:This problem describes the little to no disadvantage to the nodes in case they support multiple blockchains in the event of a blockchain split(blockchain forking). In the worst-case scenario, every fork will lead to multiple blockchains and validators will work and the nodes in the network will never achieve consensus.
Blockchains using Proof-of-Stake:
- Ethereum(Casper update)
- Peercoin
- Nxt
Variants of Proof-of-Stake:
- Regular Proof-of-Stake
- Delegated Proof-of-Stake
- Leased Proof-of-Stake
- Masternode Proof-of-Stake
Other Consensus Mechanisms in Blockchain
Beyond Proof of Work (PoW) and Proof of Stake (PoS), several other consensus mechanisms have emerged in the blockchain space. Here are some of the most prominent ones:
Delegated Proof of Stake (DPoS)
- How it works: Participants vote for representatives (witnesses) to validate blocks. These witnesses have a greater chance of being selected to create the next block based on the number of votes they receive.
- Advantages: Faster transaction speeds, lower energy consumption, and potential for greater decentralization.
- Disadvantages: Risk of centralization if a small group of witnesses control the majority of votes.
Proof of Authority (PoA)
- How it works: A pre-selected group of trusted nodes (authorities) validate blocks. These authorities are typically organizations or individuals with a reputation to uphold.
- Advantages: Faster transaction speeds, lower energy consumption, and potentially higher levels of security.
- Disadvantages: Centralized nature, as the network's security relies on the honesty and integrity of the authorities.
Proof of Capacity (PoC)
- How it works: Participants compete based on their storage capacity rather than computational power. The more storage space a participant has, the higher their chances of being selected to create the next block.
- Advantages: Lower energy consumption, potential for greater decentralization, and can be used to incentivize storage providers.
- Disadvantages: Can be less secure than PoW or PoS, as it may be easier for attackers to acquire a significant amount of storage space.
Proof of Elapsed Time (PoET)
- How it works: Participants compete based on their ability to wait a random amount of time. The first participant to wait the required time and announce their readiness creates the next block.
- Advantages: Lower energy consumption, can be used to incentivize participation, and can be more resistant to centralization.
- Disadvantages: May be less secure than other mechanisms, as it relies on the honesty of participants.
Hybrid Consensus Mechanisms
- How it works: Combine elements of multiple consensus mechanisms to address their respective strengths and weaknesses. For example, a hybrid mechanism might use PoS for block validation and PoA for consensus on network parameters.
- Advantages: Can provide a balance of security, scalability, and energy efficiency.
- Disadvantages: Can be complex to implement and may require careful tuning.
Bitcoin Mitigating Blockchain Attacks
Bitcoin is the most secure cryptocurrency, which provides security at multiple levels of the protocol. It is often rendering sustained sophisticated attacks. In this section, we are going to look at various types of probable attacks in the bitcoin system.
The Sybil Attack
The Sybil attack happens in the peer-to-peer network. A malicious attacker wishes to carry out this attack on the bitcoin network. In this, a node in the network operates multiple identities at the same time and undermines the authority in the reputation system. Its main aim is to gain the majority of influence in the network to carry out illegal actions in the system.
The Sybil attack is difficult to detect and prevent, but the following measures can be useful:
- By increasing the cost of creating a new identity.
- Require validation of identities or trust for joining the network.
- Give different power to different members.
Race Attack
The Race Attack requires the recipients to accept unconfirmed transactions as payment. As an attacker, you can send the same coin to different vendors by using the two different machines. If the vendors deliver the things without waiting for block confirmation, they will soon realize that the transaction was rejected during the mining process. The solution to this is that the vendor must wait for at least one block confirmation before sending things.
This attack is easier to pull off when the attacker has a direct connection to the victim's node. Therefore it is recommended to turn off incoming connections to nodes for receiving payments so that your node will identify their own peers. And it does not allow the payer to submit the payment to the payee directly.
Finney Attack
The Finney attack is named after Hal Finney. The Finney attack is one of the types of double-spending problem. In this attack, the attacker is the miner who mines blocks normally. In the block, he includes a transaction which sends some of his coins back to himself without broadcasting the transaction. When he finds a pre-mined block, he sends the same coins in a second transaction. The second transaction would be rejected by other miners, but this will take some time. To prevent this attack, the seller should wait for at least six blocks confirmation before releasing the goods.
Vector76 Attack
The Vector76 attack is a combination of the Race attack and the Finney attack such that a transaction that even has one confirmation can still be reversed. In this attack, a miner creates two nodes, one of which is connected to the exchange node, and the other is connected to well-connected peers in the blockchain network. Now, the miner creates two transactions, one high value, and one low value. Then, the attacker pre-mines a high-value transaction to an exchange service. When a block is announced, he quickly sends the pre-mined block directly to the exchange service. When exchange service confirms the high-value transaction, the corrupted attacker sends a low-value transaction to the blockchain network that finally rejects the high-value transaction. As a result, the corrupted attacker's account is deposited on the amount of the high-value transaction. This attack can be protected by disabling the incoming connections and only connecting to well-connected nodes.
The 51% Attack
The 51% attack is a potential attack on the blockchain network. It refers to a single miner or group of miners who are trying to control more than 50% of a network's mining power, computing power or hash rate. In this attack, the attacker can block new transactions from taking place or being confirmed. They are also able to reverse the transactions that have already confirmed while they were in control of the network, leading to a double-spending problem.
When a miner forms a valid block of transactions, the individual will broadcast the block to other miners on the network. It can only be accepted if all transactions in a block are valid according to the existing record on a blockchain. However, a corrupt minor with more than 50% of a network's hash rate does not broadcast solutions to the rest of the network. It results in the formation of two versions of the blockchain. One is the public version of the blockchain, which is being followed by legitimate miners. And second is used by the corrupt miners who are not broadcasting it to the rest of the network.

This type of attack is fictitious because it is costly to acquire computing power, which has more than 50% of the computing power of the entire network.







Late last year, I fell victim to a cryptocurrency scam. A Facebook imposter convinced me to invest a significant amount, promising huge profits through an "authorized" crypto company. Unfortunately, they took off with $153,000 worth of crypto. I was devastated, as it was my hard-earned money. After some research, I came across the RHIANNON RECOVERY LOST, a group known for their expertise in crypto recovery. They successfully helped me recover my funds, and I’m truly grateful for their assistance. I wanted to share my experience as a way of thanking them for their professionalism and support. Contact on via email: RHIANNONRECOVERYLOST@GMAIL.COM Also on WhatsApp +1 (205) 276-2470 ..
ReplyDelete